
Cloud Security
Your expert for questions

Vladyslav Dunajevski
Director, Cyber Security & Privacy, PwC Germany
Email
Full-stack security for the entire cloud life cycle
Are you planning to use cloud solutions to implement a new business or operating model, but you still need to ensure secure implementation and integration? Or maybe you’re already using cloud apps and want better management of the compliance and cybersecurity risks involved?
Our experts are here to help you establish the measures you need for cloud security. We take into account both your company’s risk profile and the level of protection that your systems and data need.
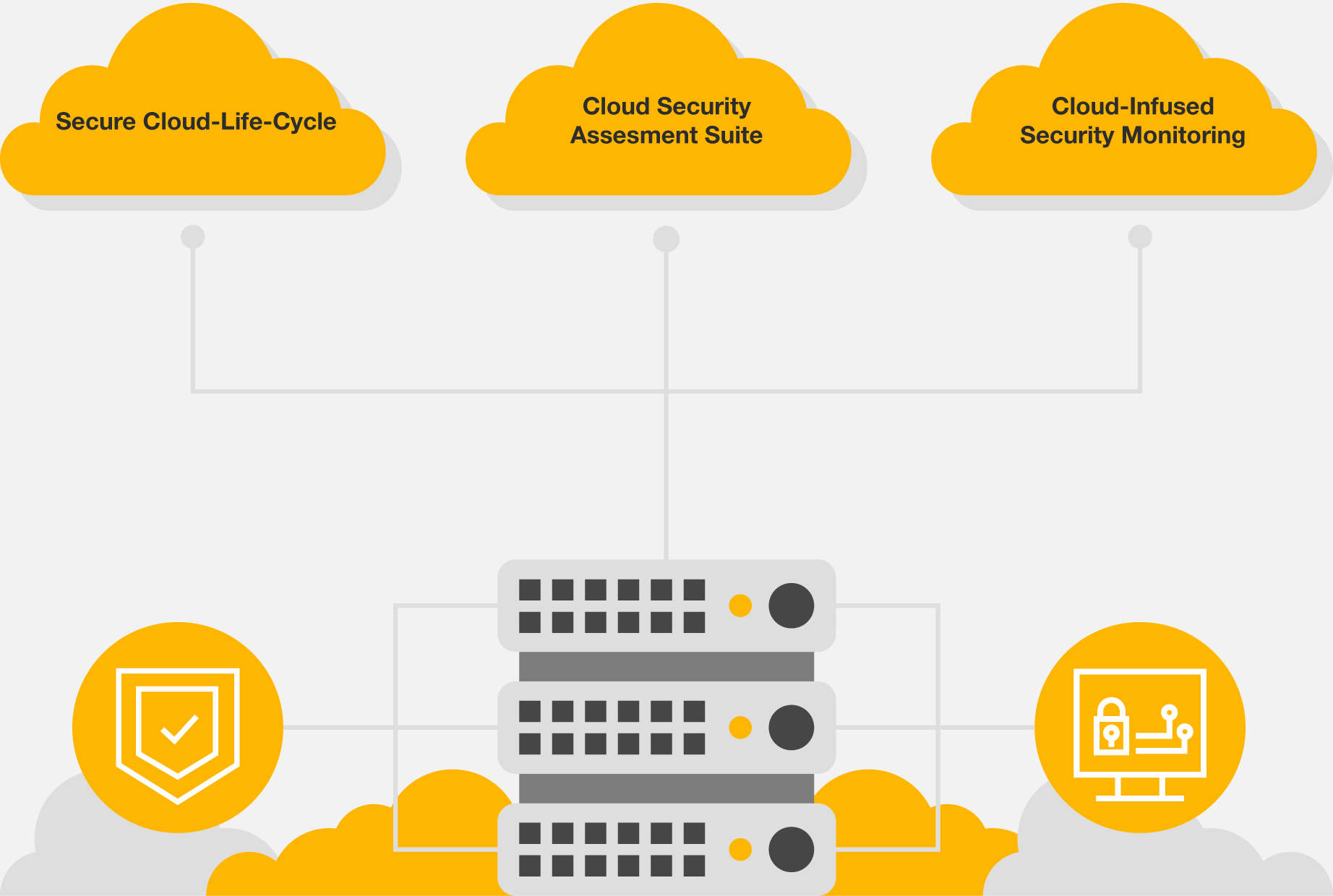
Our services at a glance
Security at every stage of the cloud service life cycle with our Secure Cloud-Life-Cycle.
Tool based security assessments with our Cloud Security Assessment Suite.
Monitoring the Cloud with Cloud-infused Security Monitoring.
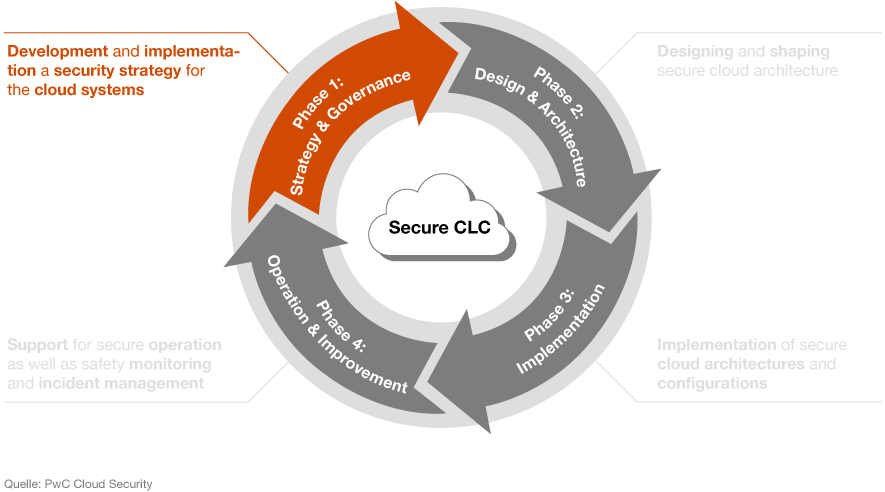
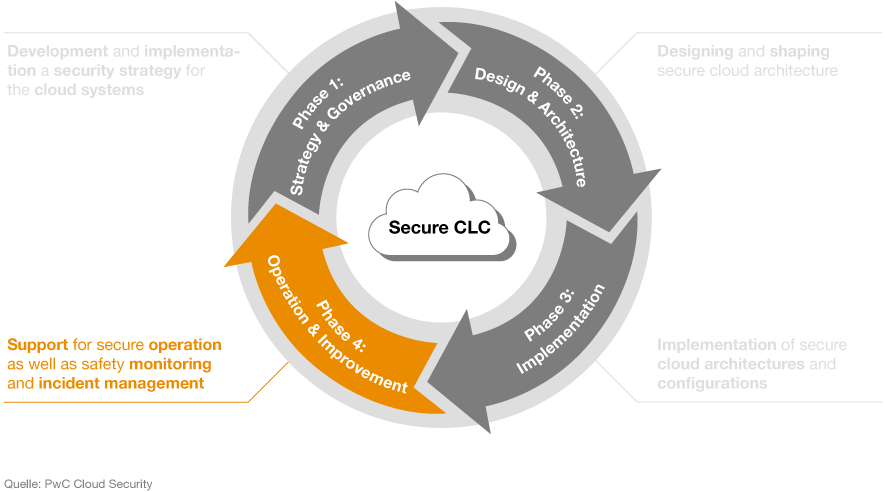
Our secure cloud life cycle concept has four phases and has been developed so that you can benefit from our security solutions throughout each phase, for both your data and your IT systems.
Secure Cloud-Life-Cycle
- Phase 1: strategy and governance
- Phase 2: design and architecture
- Phase 3: implementation
- Phase 4: operation and improvement
Phase 1: strategy and governance
We start by helping you develop and implement a new security strategy. We also provide support with the cybersecurity aspects throughout the life cycle of your company’s cloud systems.
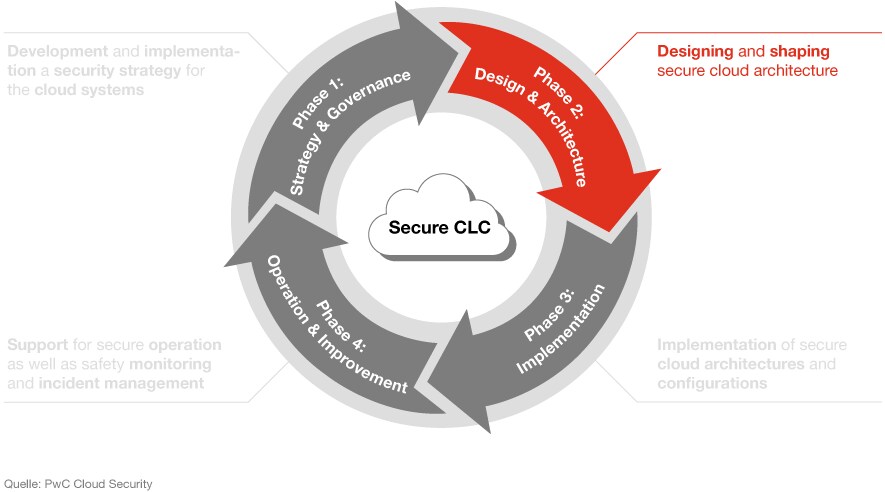
Phase 2: design and architecture
The next step is designing and shaping secure cloud architecture. We’ll guide you through this process, and help you develop a cloud security plan.
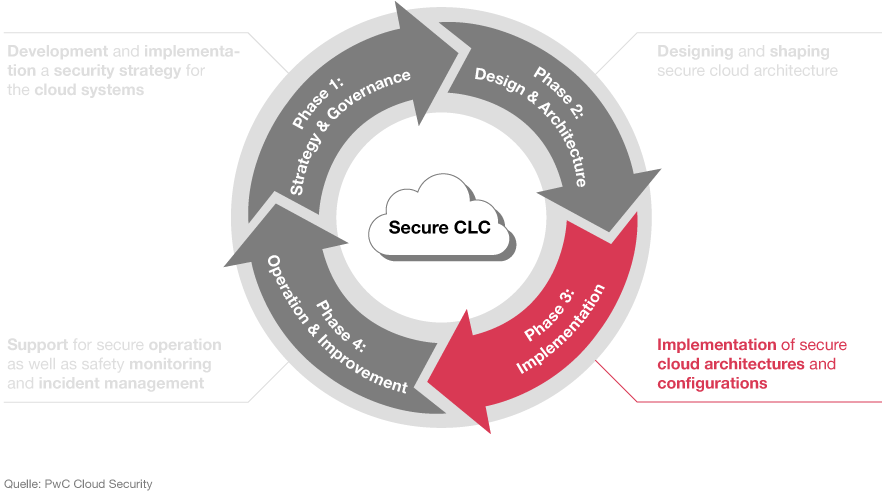
Phase 3: implementation
Once your plans are finalised, we’re here to support you in implementing secure cloud architecture. We can also help you configure secure (multi-) cloud environments, from various different providers – including hybrid environments.
Phase 4: operation and improvement
After implementation, we’ll remain on hand to help ensure secure operation of your cloud solution, along with providing security monitoring and incident management.
Cloud Security Assessment Suite
Tool-based security assessments
Our Cloud Security Assessment Suite offers a holistic approach to evaluating the security of your cloud systems, including custom security checks on both the technology and the processes you’re using. The suite helps you to identify the current level of maturity of your processes and assess how secure your cloud environment is – whichever cloud provider or service model you’re using.
Cloud Compliance & Security Inspector
Cloud technology is constantly undergoing rapid development. This makes it increasingly difficult for users to keep track of all the available cloud security configurations – let alone understand them and keep them updated.
Our Cloud Compliance & Security Inspector (Cloud CSI) Tool checks whether your security settings conform to proven standards and identifies any related weaknesses. It also enables us to see whether you’re making optimal use of all the security functions and technology offered by your cloud provider.
To ensure objectivity and risk based approach in our assessments, we use our own, independent scoring model. This model is based on our extensive experience and expertise gained from our insights into diverse cloud environments around the world.
Maturity assessment
To ensure a smooth transition to cloud solutions, it’s important to both know the current level of maturity of your relevant IT and security processes, and to define a target level of maturity. Relying on our tried-and-tested cloud security framework, our experts can help you determine the current level of maturity and identify possible risks. We’ll then create a road map based on the results to enable you to address risks, close gaps in security and improve the maturity of your processes.
Security assessment of cloud architectures
As part of our architecture assessments, we evaluate security measures for all levels of your cloud service architecture – both those which are planned and those which have already been implemented. This gives an overview of weaknesses in the architecture and generates recommendations to ensure protection against, detection of, and response to relevant cybersecurity threats.
Cloud-infused security monitoring
Monitoring cloud data flows
We can help you implement security information and event management (SIEM) solutions and migrate them to the cloud. Our experts are also on hand with our cloud monitoring implementation methodology to guide you through the full implementation and configuration process for SIEM solutions such as Azure Sentinel.
Cloud-native managed service
Azure Sentinel is our managed service for security monitoring, both for your cloud solutions and your on-premises software. Together with our security expertise, the solution’s integrated AI and machine learning functions help to considerably simplify day-to-day security operations, providing automated response processes and an outstanding reduction in false positive rates.
“More and more companies are outsourcing all kinds of business-critical applications and data to cloud providers, which makes it essential to ensure that preventive, sustainable data security and cybersecurity measures are also in place in cloud solutions.”
Vladyslav Dunajevski,CCSP, CISSP, MS-500, AZ-500, Director Cyber Security & Privacy, PwC GermanyOur expertise – your benefits
Cloud security: one of our core competencies
Our work in auditing and consulting has given us a thorough understanding of cloud computing. Our team of experts is highly experienced, with relevant knowledge in the field and various certifications – both provider-specific ones from Microsoft, Amazon and Google Cloud, and general ones such as CCSK and CCSP. This puts us in a position to evaluate and implement security measures in any cloud environment, including large-scale, multi-cloud systems.
International network
Our international network of experts and our extensive experience with international clients enable us to guarantee cloud security in any phase of the process and anywhere in the world.
Market knowledge
We have an in-depth understanding of our clients’ business models and internal processes. This enables our experts to lay solid foundations to deliver the highest possible level of cloud security, while giving top priority to your business objectives.
Our expertise extends across both public and private sectors, including the financial industry, and enables us to carry out cross-industry cloud projects while taking account of all the industry-specific factors that need to be considered.
Do you have any questions?
Contact our expert
Contact us







